How Increasing Cybercrime is Driving Innovation in Cybersecurity

Increasing cybercrime is causing significant damage to businesses. To combat this growing threat, companies are investing more in cybersecurity, but the solutions currently available commercially do not fully meet customers' needs. As a result, there are numerous innovations that are helping companies improve their security and better protect themselves from cyber threats as part of their digital transformation.
Driving Innovation in Cybersecurity: Meeting the Growing Demand
Cybercrime is on the rise, and the damage from cyberattacks is forecast to rise to around $10.5 trillion annually by 2025. While many organizations are increasing their cybersecurity budgets in response, current commercially available solutions do not yet fully meet customer demand when it comes to automation, pricing, services, and user-friendliness. The rise in IoT and edge computing brings new vulnerabilities that traditional cybersecurity products and services, such as VPNs, cannot adequately cover.
This gap is driving innovation in cybersecurity and promoting the emergence of ground-breaking solutions, such as Zero Trust Network Access.
But first, we want to explore the current trends in cyberattacks, the risks to organizations, and the issue of complexity in a rapidly changing world.
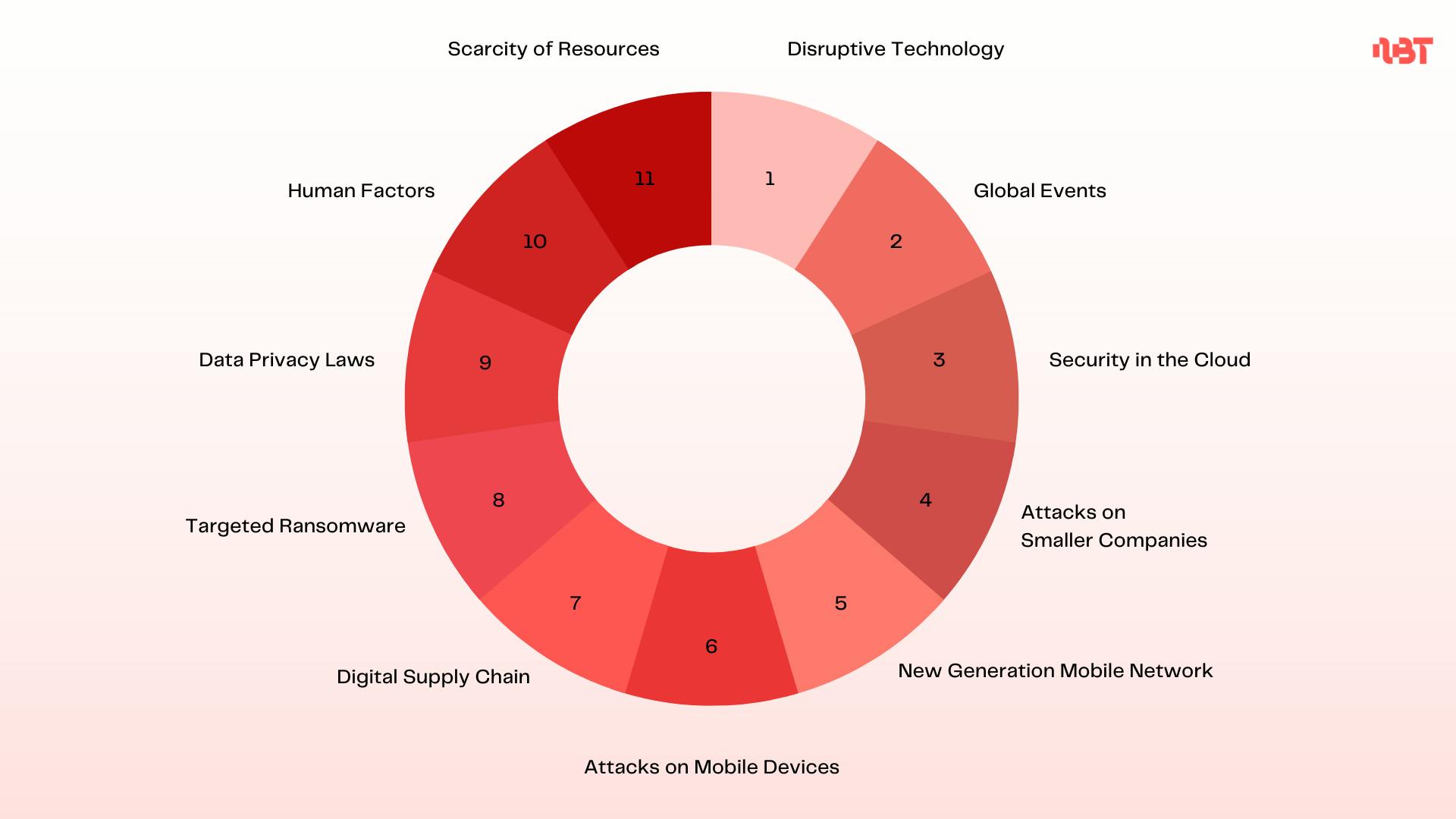
Emerging Trends in Cybercrime
There are many reasons behind the rise of attacks, and the trends in cybercrime show that companies are fighting a war on many fronts. In addition to ‘traditional’ cyberthreats such as phishing, organizations are now facing additional risks. Here are some of the emerging trends in cybercrime:
Disruptive technology
With open-source AI now available, it’s increasingly easy to create deep fakes or voice clones, and otherwise use social engineering to do harm. The increased use of IoT technology, and a shift to interconnected IoT environments, also creates vulnerabilities.
Digital supply chain
Your company is only as secure as your weakest digital supplier. Connected to the emergence of disruptive technology is the risk from a digital supplier. Companies are relying on a myriad of digital tools, some of which can be accessed remotely.
The ‘human factor’ in cybersecurity – social engineering and burnout
Cybersecurity goes beyond computer systems and networks. One of the most significant vulnerabilities is the people who use these systems. This includes attacks using ‘social engineering’, that exploits human beings’ natural instincts – fear, trust, or respect for authority, but also increased stress on IT professionals due to overwork, and the resulting burnout. The interconnection between technology and humans is increasingly important, as companies battle to recruit and retain talent.
Attacks on smaller companies
While larger organizations often have the budget and capabilities to withstand a cyberattack, small and medium-sized businesses may face more significant – potentially even fatal – consequences. These companies are also more likely to be targeted, as they are seen as less likely to have advanced security systems in place.
Identifying cyber vulnerabilities in a complex environment
In a complex, interconnected world, it can be difficult for companies to determine exactly where their largest vulnerabilities lie, in order to assess and design a response to the threat of cyberattacks.
The trends mentioned above are interlinked. For example, as companies look for ways to ease their employees’ workload or enable popular working-from-home options, they rely on external service providers for AI or remote working services.
Internal silos, for example, between operational technology systems and the IT team, present a significant risk, as do external links to partners. A recent survey revealed that over 94% of organizations had some sort of security incident in the previous six months that impacted their industrial IoT infrastructure. Furthermore, 87% of those affected said their operations were impacted for at least one day.
The current complex threat landscape requires a dynamic and holistic approach to cybersecurity.
Increased cyberattacks spark innovation
Companies of all sizes and locations are prioritizing cybersecurity, and this increased demand is powering a boom in creativity and innovation. McKinsey forecasts that spending on products and services in the cybersecurity industry is set to rise 13% annually up to 2025. This included significant increases in services and the SMB segment, as even smaller and medium-sized companies become more aware of the risks.
Innovations in Zero Trust
As companies increasingly move to cloud-based environments, the demand is growing for products and services that enable sharing across environments, without compromising cybersecurity, with a focus on Zero Trust principles, and an identity and data-centric security approach. Zero Trust isn’t a tool or an app. It is an approach to security, based on seven core principles:
- Treat everything as a resource - All data sources and computing services are considered resources.
- Secure all communications - All communication must be secured, regardless of network location.
- Maintain session-based access - Access to individual resources is granted on a per-session basis.
- Policies must be dynamic - Access to resources is determined by dynamic policies which respond in real-time to changing security posture.
- Continuously monitor security posture - No asset is inherently trusted because of who, where or what it is, or was. The security of resources is a point-in-time state and should be continuously evaluated.
- Authenticate before connect - Resource authentication and authorization is dynamic and strictly enforced before access is granted. This means actors, systems, and workloads (resources) inside the perimeter should not be automatically trusted. Without verification and policy-based authorization, access is denied.
- Measure and improve - Collect as much data as possible. Monitor and measure the integrity and security posture of all assets and use it to improve.
One such innovative company in Zero Trust is Enclave, an investment of NBT, which enables connections between apps, staff, developers, cloud, and IoT devices without VPNs, opening firewalls, adding edge devices, or changing infrastructure. Clients are particularly impressed with the ease of use of Enclave, with the provision of simple, safe, and secure private access, without VPNs or firewalls slowing communication to a crawl.
Innovations in edge computing
Edge computing is an emerging computer paradigm which refers to a range of networks and devices at or near the user. Traditionally, data would be sent to a centralized data center for processing, but edge computing moves some portion of the storage and computes resources closer to the data source, for example, the autonomous vehicle or digital healthcare device.
Another NBT portfolio company, weeve, addresses several of the current cybersecurity threats in IoT, including data privacy and the shortage of IT experts to create new applications. weeve provides an IoT Edge Application building platform that allows customers to easily create IoT apps and gain insights from the data generated by their machinery. The platform requires no coding knowledge, making it accessible to businesses of all sizes.
Innovations in partner ecosystems
Supply chain security relies on a trusted partner ecosystem. As these are becoming increasingly complex, innovative companies are increasingly working together to offer their clients ‘bundles’ of products or services. Demand for these full-service offerings is set to rise by as much as 10% over the next few years. According to McKinsey, providers that focus on outcomes, not technology, will be particularly effective, and partners should build collaborative sales capabilities.
The partnership between Enclave and weeve, for example, provides clients with secure access to their IoT implementations and improves ROI.
As companies around the world move forward in their digital transformation journeys, cybercrime will continue to be a factor. While organizations have at times limited ability to respond to global influences, such as the lack of qualified IT talent, they can take advantage of the innovations in cybersecurity in the coming years.




